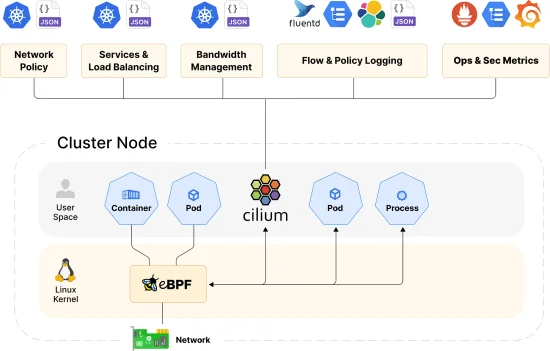
Exploring Cilium: Revolutionizing Network Security and Observability
Learn about Cilium, its features and how to use Cilium in Kubernetes
Learn about Cilium, its features and how to use Cilium in Kubernetes
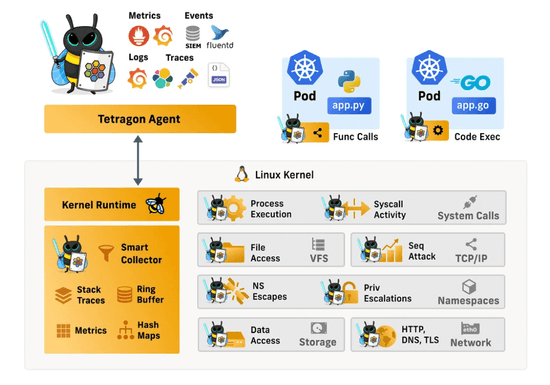
Explore eBPF fundamentals and Tetragon's role in real-time security monitoring in cloud native setups, especially Kubernetes. Explore Tetragon's architecture and functionalities, its capability for deep system insights without altering applications, and its integration with tools like Prometheus and Grafana for advanced analysis
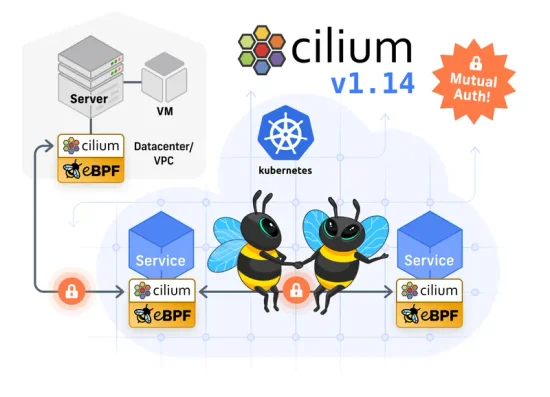
Dive into how to get Cilium mutual-auth working on a self-managed cluster
Dive into this article detailing how the author migrated from a combination of Flannel, Nginx Ingress, MetalLB, and kube-proxy to embracing Cilium as an integrated solution for networking, load balancing, and network security
Plongez dans les principales fonctionnalités et améliorations du nouveau cilium 1.14
Dive into some of the features and functionality in the Cilium 1.14 release, starting by installing Cilium, then working through deny policy and debugging with Hubble
Learn about the overlayfs upstream vulnerability in the kernel and how to prevent the escalation of the vulnerability using Tetragon
Delve into how Cilium can be used alongside the security groups for EKS pods in supported clusters when running in chaining mode
Learn how the AKS-managed kube-proxy DaemonSet can be disabled to support BYOCNI (Bring your own CNI) and install Cilium as the CNI
For live conversation and quick questions, join the Cilium Slack workspace. Don’t forget to say hi!
Join slack workspace